RAJ GETS QUOTED IN AN ARTICLE ON SECURITY
Article by Daniel Humphries
In 2015, millennials will become the largest demographic in the workforce, with a population of over 75 million. Security experts are concerned that this group’s attitudes toward privacy, combined with expectations regarding what devices and apps they can access at work, will bring new cybersecurity challenges to the workplace.
Software Advice surveyed employees from three different demographics—“millennials” (those born after 1980), Generation X, or “Gen X” (born from 1965-1980) and “baby boomers” (1946-1964)—on their attitudes toward security issues. In this report, we look at the impact generational attitudes have on behavior and whether millennials really do expose businesses to heightened risk. We also provide advice on how companies can stave off that risk.
Key Findings:
- Millennials have the worst password reuse habits of all demographics: 85 percent admit to re-using credentials across sites and services.
- Risky behavior can be found across demographics: 16 percent of millennials and 14 percent of Gen-Xers accept social media invites from strangers “most of the time.”
- Boomers may in fact pose a bigger BYOD challenge than millennials: 48 percent of the former use personal devices to access work files, versus 40 percent of the latter.
- Millennials are most likely to find security workarounds: A combined 56 percent admit they would “very” or “moderately likely” evade restrictive workplace controls.
- Millennials are less interested (15 percent) in receiving security training through “gamification” than Gen-Xers (18 percent), while boomers prefer lectures (44 percent).
Introduction
The rise of the millennials—the allegedly tech-savvy, superconnected segment of the population—is leaving some security experts profoundly anxious.
For instance, Andrew Avanessian, vice president of Global Professional Services at security firm Avecto, describes them as nothing less than a “a new attack vector that is emanating from the inside.”
Author and security expert Steven Weisman is also concerned: He considers millennials “a tremendous risk to the data security of their employers.” But why the concern?
“Millennials are tremendously comfortable with, and active users of, great amounts of social media—but unfortunately, do not often do so with the proper security precautions, which can lead to data breaches,” Weisman explains.
This pessimistic perspective is not universal, however. For instance, Joe Siegriest, CEO of password management firm LastPass, states that “millennials are not any more of a threat than any other generation.”
So, do we stand on the brink of techno-armageddon? Are elders really better when it comes to cyber-security? Let us use statistics to shine some light on the matter.
Millennials Are Serial Offenders When It Comes to Password Reuse
We begin with the basics: password reuse. After all, once compromised, credentials recycled on different accounts may give cyber-crooks access to sensitive information.
But which demographic is most likely to reuse passwords?
Have Reused Passwords in Past 12 Months

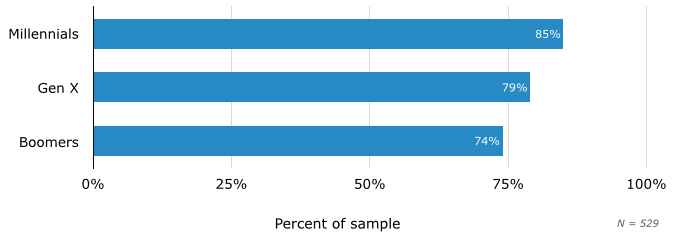
Here, millennials come out in front, with 85 percent admitting to reusing passwords. However, Gen X lags only six percentage points behind, at 79 percent, while almost three-quarters (74 percent) of boomers are guilty of the same bad habit.
So are millennials inherently more cavalier regarding password security? Not necessarily: assuming millennials use more online services and apps than their parents and grandparents, they will have a greater quantity of passwords to remember. So it’s no surprise if they reuse some of them. So what is to be done?
Siegrist suggests that “Businesses should put the tech-savviness of millennials to work for them.”
For instance, employees can be encouraged to use password managers, which create unique credentials for all accounts, but that can be managed through one, ultra-strong master password. Given that password reuse is endemic, this is a tool every employee should use—not just those born after 1980.
Businesses can also implement two-factor authentication, which combines a password with a randomly generated number that is sent to the user and that changes at each login, thus rendering compromised credentials useless.
Siegrist suggests that this could be an easier sell to millennials who are attached to their smartphones. For instance, it can be as simple as installing an app on a phone: The app will generate the second factor for the user, reducing the need to rely on text messages or emails.
Millennials, Gen X Almost Equally Risk-Prone With Social Media Use
Social media can provide criminals with a rich trove of information to be deployed in phishing attacks on businesses. Some experts fear that millennials’ more relaxed attitude toward online privacy increases this risk.
“People who grew up oversharing on social media often do not comprehend, from a practical level, the full gamut of what they should not be sharing—even after being told of privacy and confidentiality policies,” says cybersecurity expert and Forbes contributor Joseph Epstein. “They simply do not have the same sensitivities as prior generations.”
So next, we asked respondents how often they accept invitations from complete strangers on social media, thereby granting them access to the personal information in their profiles.
Frequency of Accepting Social Media Invitations From Strangers



Here, millennials are only marginally ahead of Gen X and the boomers, with 3 percent “always” accepting invites versus 2 percent in both older demographics. This close alignment suggests that it is less a question of generational attitudes and more that there is always a small subset of individuals in the wider population who are excessively open or trusting.
In the next-riskiest category, millennials and Gen X are closely aligned, with 16 percent and 14 percent accepting invites “most of the time.” Only the boomers show heightened concern, with a mere 8 percent accepting such invites “most of the time”—and a further 50 percent “never” doing so, versus 38 percent of millennials and 42 percent of Gen-Xers.
Is the prevailing image of millennials as over-sharing naifs exaggerated? Security expert Todd Inskeep, who sits on the advisory board of the RSA Conference, thinks so:
“The cultural environment has changed—people are more open. This openness isn’t generational, it’s cultural, and applies to people of all ages,” Inskeep explains.
In addition, some social media platforms may be riskier than others. According to Kevin Epstein, vice president of information security and governance at security firm Proofpoint, phishing scams using fake LinkedIn templates are twice as successful as any other social media scam. Meanwhile, according to the Pew Research Center, the demographics of LinkedIn users skew older.
LinkedIn users also outnumber the generally younger Twitter demographic: 300 million to 271 million. Thus, since boomers and Gen-Xers and Boomers are more active on LinkedIn, gains from whatever relative caution they may display could be nixed by the higher degree of phishing danger associated with the platform.
It’s little wonder then, that Mark Orlando, director of cyber-operations at security firm Foreground Security, argues that we should “ditch stereotypes.” Orlando suggests something simple: All users, regardless of age should be encouraged to treat information in social networks “the same way they would their finances: Be aware of who has access to it, how it’s being used and, most importantly, how and to whom it is distributed.”
Mature Demographics May Pose a Higher BYOD Risk
One trait widely associated with millennials is their devotion to devices: Indeed, so intense is the relationship that a new term—“nomophobia”—has been coined for the anxiety that arises when separation occurs. In one study, 40 percent of millennials said they would feel “anxious, like part of me is missing,” if they were separated from their smartphones.
This expectation of instant access through devices also applies to their professional lives, says Elise Yacobellis, director of development for the IT security certification organization (ISC)².
“Millennials … in all industries are focused on accessibility to information at work,” she says. “They grew up with technology at their fingertips, and they won’t expect any less in their work environments.”
However, the Bring Your Own Device (BYOD) phenomenon, in which employees use their personal devices for work purposes, also heightens risk, as personal smartphones and tablets rarely have the same level of protection as technology placed behind a corporate firewall. But are millennials really the worst offenders?
Frequency of Using Personal Devices to Access Work Documents



In fact, older demographics may be more inclined to obscure the work/personal divide. Forty-seven percent and 48 percent of Gen-Xers and boomers, respectively, admit to accessing work documents on personal devices “very often,” versus 40 percent of millennials.
Could it be that millennial tech savviness is a myth? Frank Bradshaw, CEO of cybersecurity consultancy Ho’ike Technologies suggests that it may be exaggerated.
“Remember, the people calling them ‘tech-savvy’ are Generation X and older. … A group of people that spent a great deal of their 20s and 30s marveling [at] how six-, seven- and eight-year-olds could figure out technology. The reality is technology was made exponentially easier by each passing decade,” he explains.
However, even Bradshaw agrees that millennials as a group are “completely mobile.” Perhaps the line between work and personal computing is more blurred among older demographics because they are more likely to be in managerial positions, working at home in the evenings, or toiling away at high priority projects on weekends.
So, what to do?
Todd Peterson, product marketing manager for Identity and Access Management at Dell, suggests:
“Allow employees to access work information from wherever they are and with whatever device they want, but maintain control of that access and only grant it where it’s absolutely necessary.”
To achieve this, firms can provide users with a list of approved apps and implement document control, limiting which resources employees can access using their own devices.
“Users should stick to well-known, reputable application marketplaces and pay attention to the features and information accessed by new apps. Again, personal and professional separation is key, whether or not there are mobile or BYOD controls in place,” adds Foreground Security’s Orlando.
This means no haphazard downloading of freeware found floating on the Internet. Rather, users should stick to reputable outlets, such as Google Play or the Apple App store.
As for policies defining use, Yacobellis says that as long as they are “sensible, well-balanced and enable business efficiency” there shouldn’t be concern: “The key is awareness and training, along with an explanation of why the policies are important,” he notes.
For instance, it should be easy to explain to employees why their devices must be password-protected, and that these passwords must be strong (e.g., at least eight characters, with a mix of numbers and special characters).
Millennials More Tempted to Use ‘Workarounds’ to Evade Workplace Controls
Regardless of what protections are in place, however, Dell’s Peterson suggests there may be another potential security problem associated with millennial employees who tend to have a “‘just get the job done’ mentality:
“This presents risk, because people will look for ways around security if they perceive security as a barrier,” he says.
Of course, employees may also look for workarounds simply because they object to having access to their favorite apps or social media restricted while at work. But is it only millennials who are likely to search for ways to circumvent the rules?
Likelihood to Use Security ‘Workarounds’



Perhaps not: 15 percent of millennials say they are “very likely” to find a way around security controls they consider too restrictive, versus 13 percent each of Gen-Xers and boomers. This close correspondence suggests the existence of a defiant personality type in every generation.
The results for “moderately likely” tell a different story. Here, 41 percent of millennials—versus 29 percent of Gen-Xers and 15 percent of boomers—say they are willing to consider finding a workaround. Perhaps facility with technology is the significant factor here: A generation with greater familiarity with these tools is more likely to consider each situation on a case-by-case basis, whereas those without the required skills will not even try.
It is a serious problem, says Paul Caiazzo, chief security architect for risk management and compliance firm TruShield Security Solutions. Caiazzo says that in his experience, “tech-savvy employees” are adept at finding tools to circumvent (for instance) restrictions placed on their social media use. However, he adds that even if a corporation does succeed in blocking all social traffic, it “runs the risk of alienating these young professionals.”
Users may also be sending confidential information outside the network, Caiazzo continues. Here, the “most mature organizations” combat the problem by combining endpoint monitoring with intelligent content-based filtration and alerting businesses when sensitive information goes AWOL, but “this technology must be well-configured and must not be seen as a silver bullet.”
In short, as with all information technology security issues, a business must protect itself through both training and technical controls.
Generations Split on Security Education Preferences
Clearly, all demographics are prone to risky behavior, and employees of every age need training. But do different generations have different preferences on how they like to receive it?
Preferred Methods for Receiving Security Training



Here, the greatest differences are between the boomers and the two younger demographics. Boomers still appreciate the traditional lecture-based method, with 44 percent saying that they prefer “in-person talks.” Millennials and Gen X, however, prefer to receive their training online.
Raj Goel, who supplies firms with security training through his company Brainlink, has additional pointers. Older people tend to read, he says, while younger employees prefer videos. Thus, he provides older employees with articles, and shows short YouTube clips when dealing with a younger audience. In addition, Goel says he tailors his case studies and examples so they are relevant to the audience.
For instance, with “college kids and new hires,” he will use illustrations tied to users’ personal lives, focusing on how, following sloppy social media habits, “kids have been kicked out of school, lost jobs, lost dates, been fired, etc.”
For 40-somethings, he will choose such themes as “how to parent in the age of Google” or “how companies have lost hundreds of thousands of dollars through payroll theft.” For those in their 60s or older, meanwhile, he will select themes such as “scams to avoid.”
Conclusions
While millennials demonstrate riskier behavior in some areas, they are not a uniquely dangerous demographic, and all generations pose serious security challenges. Likewise, every demographic has a role to play in reducing risk.
And so, instead of struggling in vain to stamp out millennial habits—and as our survey shows, those of older generations, as well—firms should seek to harness them. They can offer additional tools, such as password managers or two-factor authentication, or provide anti-phishing training, while explaining why these defenses are important.
The security challenges businesses face are growing, and the easier firms make it for their employees to help with that task, the greater the likelihood of success in the fight against cybercrime. Organizations must embrace every tool and approach available to them, partnering with all of their employees in the fight against cybercrime.
Methodology
To find the data in this report, we conducted an online survey of 529 employees of U.S. businesses who used computers in their daily work, filtering the total into demographic subgroups by date of birth. We asked eight questions, and collected 529 responses per question. All survey questionnaires undergo an internal peer review process to ensure clarity in wording.
Sources attributed and products referenced in this article may or may not represent partner vendors of Software Advice, but vendor status is never used as a basis for selection. Interview sources are chosen for their expertise on the subject matter, and software choices are selected based on popularity and relevance.
Expert commentary solely represents the views of the individual. Chart values are rounded to the nearest whole number.
Source: http://www.softwareadvice.com/security/industryview/millennial-threat-report-2015/

